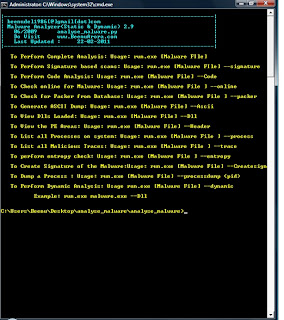
Malware Analyzer - A tool developed by Beenu Arora to perform static and dynamic analysis of malwares.
The static analysis allows analyst to predict the behaviour of malware without actually executing it which in turns saves resources in terms of time and effort. It can be useful for string based analysis for Windows registry, API calls, IRC Commands, DLL’s called and anit-VMWare code detection. It can perform a full ASCII dump of the PE along with other options. It can also generate various section of a PE. Malware analyzer also assists on the code analysis of the malware. It can also perform an online malware check. Based on PeID signatures, it can also detect packers used to compress it. It also provides a tracer functionality that can be used to identify anti-debugging calls tricks, file system manipulation calls, Rootkit hooks, keyboard hooks, DEP setting changes, Hardware Breakpoints,Internet communication etc generally used by malwares. It also performs the CRC and timestamp based verification to detect any anomalies along with entropy based scan for identification of malicious sections. The tool can be used to create signatures of a malware which then can be exported as custom signature of AV or IDS. It also allows viewing modules of process along with complete process dumping.
The Dynamic analysis allows predicting the actual behaviour of the malware at runtime. Currently malware analyser allows hooking to certain APIs File creation and Registry creation and more to come near future.